My First Splunk Dashboard
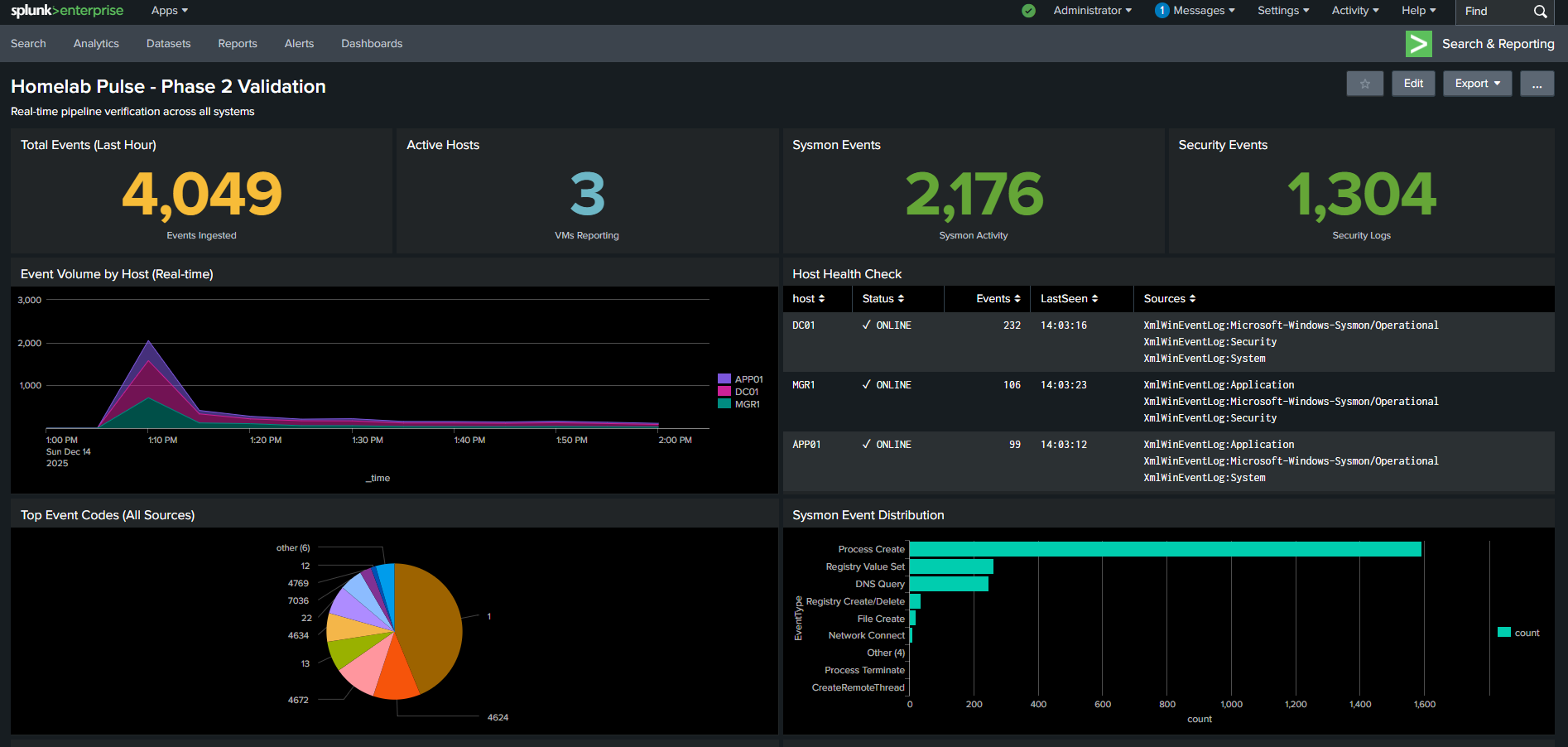
Complete Security Monitoring Dashboard
Real time visibility into log ingestion health, authentication activity, and endpoint behavior across the homelab environment.
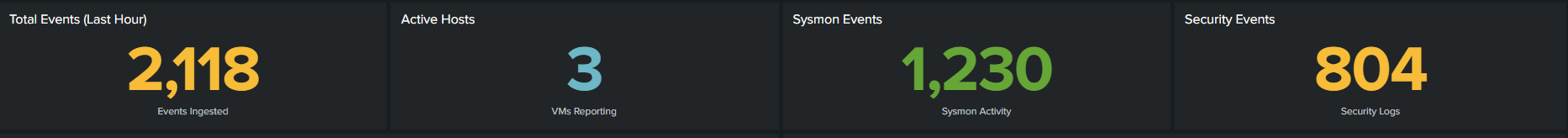
Quick Stats: The "Is It Working?" Panel
Total events, active hosts, Sysmon activity, and Security log volume at a glance.
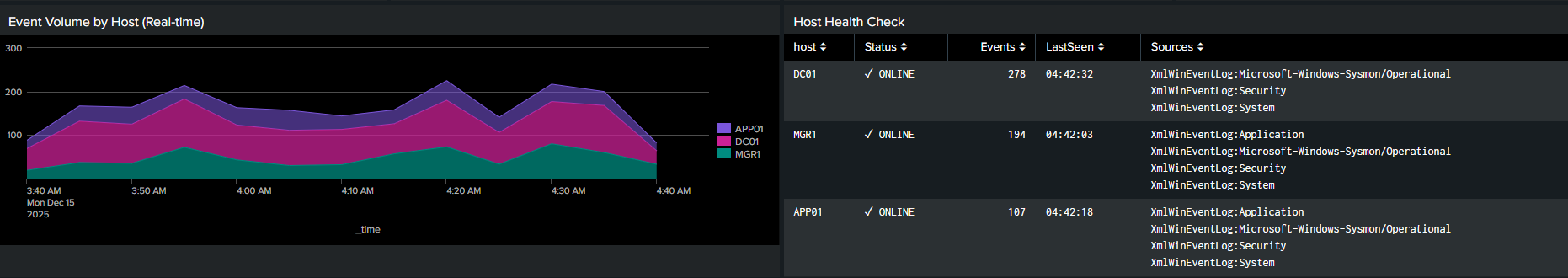
Host Validation & Health Checks
Event volume by host over time + health status table. Identifies quiet endpoints and validates consistent log forwarding.
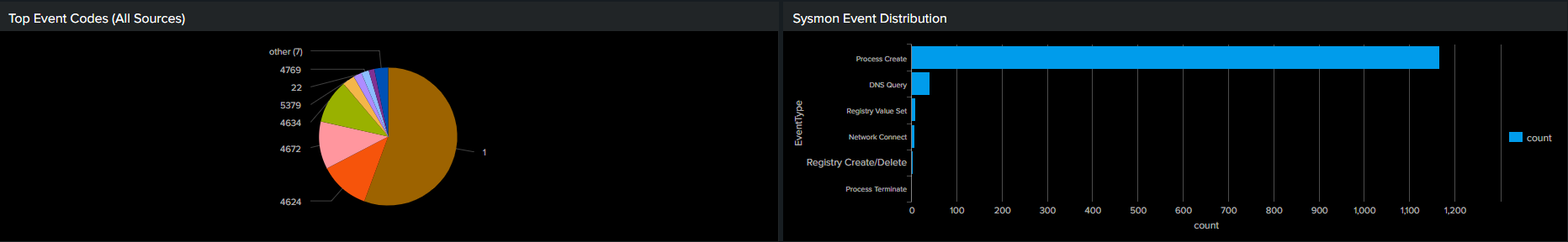
Event Type Analysis
Top event codes across all sources + Sysmon-specific distribution.
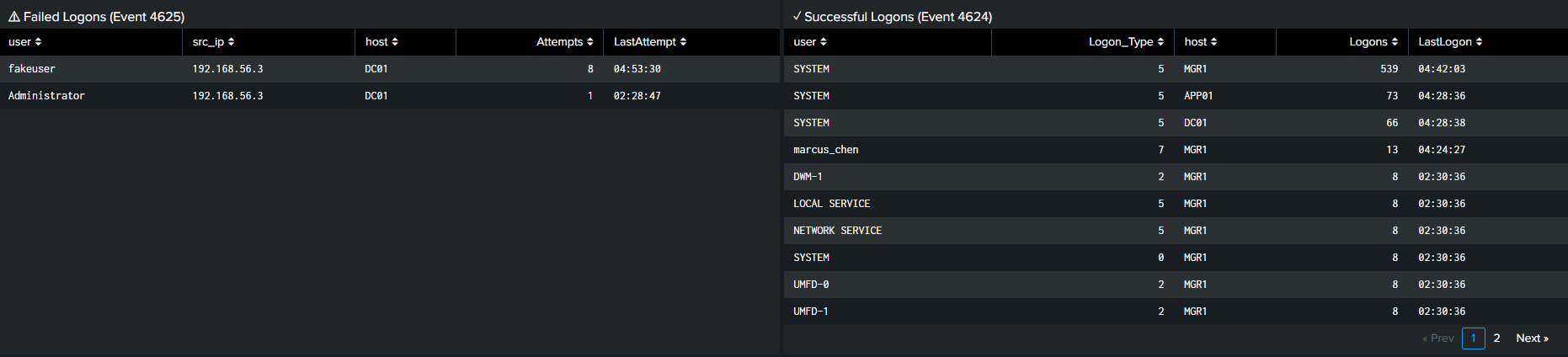
Basic Security Monitoring
Failed logons (4625) vs. successful logons (4624) with filtering out network logons that clutter the view.